Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Malware
"Pipedream" Malware Targets ICS: What Critical Infrastructure Owners Need to Know
Troubling new malware designed to facilitate attacks on a wide array of critical infrastructure – from oil refineries and power plans, to water utilities and factories – is raising concerns for its versatility. The malware, named Pipedream by Dragos and Incontroller by Mandiant, who have both tracked and researched the toolkit, is potentially capable of gaining full system access to multiple industrial control systems (ICS) and supervisory control and data acquisition (SCADA) devices.
ALPHV: Breaking Down the Complexity of the Most Sophisticated Ransomware
In our new threat briefing report, Forescout’s Vedere Labs describes how it analyzed files and tools used by an affiliate of the ALPHV ransomware group during an attack. ALPHV, also known as Black Cat, is a Ransomware-as-a-Service gang that was first discovered in November 2021.
Choosing the Right Metadata Store: Part 3
Part 1 of this series covered the challenges Rubrik initially faced with its distributed database. Our applications had become quite complex to work around some of these challenges. Part 2 of this series covered how we chose a new distributed database (CockroachDB), and how we performed the migration. Next, we will dive into some of the challenges we faced after migrating to CockroachDB and how we developed on top of CockroachDB to mitigate them.
LemonDuck Targets Docker for Cryptomining Operations
The recent cryptocurrency boom has driven crypto prices through the roof in the last couple of years. As a result, cryptomining activities have increased significantly as attackers are looking to get immediate monetary compensation. According to the Google Threat Horizon report published Nov. 29, 2021, 86% of compromised Google Cloud instances were used to perform cryptocurrency mining.
REvil reborn? Notorious gang's dark web site redirects to new ransomware operation
Sometimes referred to as Sodinokibi, the notorious REvil ransomware-as-a-service (RAAS) enterprise was responsible for a series of high profile attacks against the likes of the world’s biggest meat supplier JBS Foods and IT service firm Kaseya. However, it looked like its activities had come to a halt after law enforcement agencies pushed REvil offline in October 2021, and Russia reportedly arrested 14 of the gang’s members earlier this year.
Ransomware Attacks Vs. Data Breaches: What's the Difference?
Ransomware attacks and data breaches seem to be continuously contending for the top positions in news feeds. But what's the difference between these cyber threats and which should you be most concerned about? For a comprehensive breakdown of each type of cyberattack, read on.
The Upsurge in Ransomware Attacks in Australia and Opportunities to Protect Data
There are rare occasions when you open the news and don't find anything about cybersecurity in the headlines. According to the Australian Cyber Security Centre (ACSC), Australia has dealt with a cyberattack every 8 minutes in the financial year 2020-21, with over 67,500 cases of cybercrime registered in the same year. Studies indicate that ransomware is one of the most frequent and damaging types of malware leveraged by cybercriminals.
Info Stealers Ecosystem Introduction
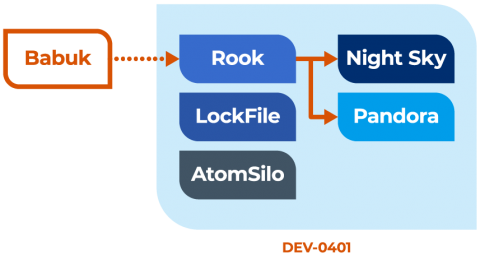
Night Sky: A Short-Lived Threat from a Long-Lived Threat Actor
In a new threat briefing report, Vedere Labs analyzes the behavior of the Night Sky malware on two samples, presents a list of IoCs extracted from the analysis and discusses mitigation. The Night Sky ransomware was first reported on January 1, 2022. Victims were asked to contact the attackers to pay for the ransom. If the victims refused to pay, attackers threatened to expose their data on a leak site.