Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Malware
Vidar Malware Launcher Concealed in Help File
Appending a malicious file to an unsuspecting file format is one of the tricks our adversaries use to evade detection. Recently, we came across an interesting email campaign employing this technique to deliver the info stealer Vidar malware. First, let’s examine the email delivery mechanism, then go on to take a closer look at the Vidar malware itself. Figure 1: The malicious spam message The messages in this campaign have two things in common.
Outpost24 webinar - The State of Ransomware in 2021 and How to Limit Your Exposure
AvosLocker ransomware - what you need to know
AvosLocker is a ransomware-as-a-service (RaaS) gang that first appeared in mid-2021. It has since become notorious for its attacks targeting critical infrastructure in the United States, including the sectors of financial services, critical manufacturing, and government facilities. In March 2022, the FBI and US Treasury Department issued a warning about the attacks.
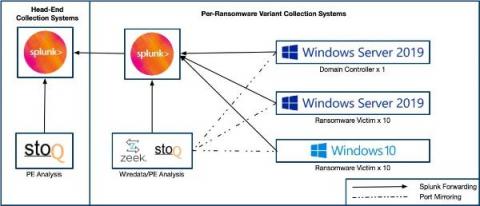
Gone in 52 Seconds...and 42 Minutes: A Comparative Analysis of Ransomware Encryption Speed
Do you feel like every other cybersecurity news story mentioned ransomware in 2021? Does it feel like you can’t turn on a cybersecurity podcast and not hear the “R” word? We feel the same way, and as a cybersecurity vendor, we felt that we should also contribute to the noise. :-) But we did want to try and do something different.
Choosing the Right Metadata Store: Part 1
Rubrik CDM is scale-out and fault-tolerant. Our software runs as a clustered system consisting of multiple nodes, where each node runs an identical copy of our software stack; each node is equally able to perform operations like data protection and recovery. To increase capacity a user simply adds more nodes. The system continues to operate when a node fails, other nodes pick up the workload while the node is offline. Scale-out, fault-tolerant products are built on distributed systems.
Analyzing Exmatter: A Ransomware Data Exfiltration Tool
Having conducted more than 3,200 incident response engagements in 2021, Kroll’s Threat Intelligence team now tracks more than 200 ransomware threat actor groups. Kroll’s global Incident Response teams are very familiar with actions traditionally associated with a network intrusion, from initial access to lateral movement to privilege escalation to data exfiltration—and in the case of financially motivated actors, ransomware deployment.
Office Documents and Cloud Apps: Perfect for Malware Delivery
Microsoft Word, Excel, PowerPoint, and other Office document formats are popular among attackers, who abuse them to infect their victims with ransomware, infostealers, backdoors, and other malware. In this article, we look at the anatomy of a recent Office document attack from the victim’s perspective, highlight the most common types of Office document attacks seen today, and suggest strategies to reduce your risk of becoming the latest victim.
Frequently Asked Questions about Rubrik Cloud Vault
At the Rubrik Data Security Spotlight, we introduced Rubrik Cloud Vault, our fully managed, secure, and isolated cloud vault service built on Microsoft Azure. Rubrik Cloud Vault enables customers to build a comprehensive and multi-layered data protection strategy to be cyber resilient.