Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Malware
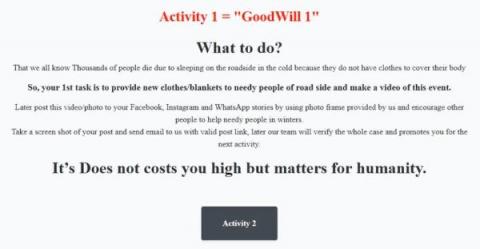
GoodWill Ransomware? Or Just Another Jasmin Variant?
In March 2022, researchers spotted a new ransomware family named GoodWill, with a new method to collect the ransom. Instead of requesting payment through crypto coins like other threats such as Night Sky or Hive, GoodWill requests that its victims help vulnerable people by following a sequence of steps, such as donating clothes, feeding less fortunate children, or providing financial assistance to hospital patients.
Can Macs Get Ransomware? Examples + Prevention Strategies
Many of the most prolific ransomware attacks to hit the news, such as Wannacry and Petya in 2017, affected PC users only. The distinct absence of Apple computers in the long list of victims has many Mac users wondering if ransomware attacks are a cyber threat they need to worry about. Can ransomware affect Macs? Short answer: Yes. While rare, security researchers have noted examples of Mac-compatible ransomware variants.
Coffee Talk with SURGe: 2022-MAY-31 Follina MSDT zero day, ransomware roundup, supply chain risk
5 ways to prevent Ransomware attacks
“Ransomware has become the enemy of the day; the threat that was first feared on Pennsylvania Avenue and subsequently detested on Wall Street is now the topic of conversation on Main Street.” Frank Dickson, Program Vice President, Cybersecurity Products at IDC.
New Black Basta Ransomware Group
What Does Defense-in-depth Mean and How Does it Bring Infrastructure and Data Security Together?
With the rise of ransomware and cyber attacks, the term defense-in-depth has risen to the forefront, but what exactly does it mean? At its core, defense-in-depth is a protection mechanism for network security–an approach that involves layering or using multiple controls in series to protect against possible threats. This layered concept provides multiple redundancies in the event systems and data are compromised.
Ransomware: 2023's top attacks and need-to-know stats
As we navigate through 2023, ransomware attacks continue to grow in scale and sophistication. This year has already witnessed an alarming number of high-profile incidents (at the time of writing), meaning ransomware attacks remain one of the most significant cybersecurity threats organizations face.
How to Decrypt Ransomware (with 100% Free Tools)
Ransomware attacks are dominating news headlines, with ransomware-as-a-service (RaaS) operators actively seeking to exploit network vulnerabilities and infect unsuspecting victims. The healthcare sector and financial industry are especially vulnerable to ransomware attacks, as they store valuable personally identifiable data (PII) which can be misused to carry out lucrative crimes, like identity theft and fraud.
Emotet Analysis: New LNKs in the Infection Chain - The Monitor, Issue 20
Kroll has been tracking Emotet since it was first identified in 2014, especially during its transition from a banking Trojan designed to primarily steal credentials and sensitive information to a multi-threat polymorphic downloader for more destructive malware. Today, Emotet operators stand as one of the most prominent initial access brokers, providing cybercriminals with access to organizations for a fee.