Webinar: Elevating Your MSP Security Practice with a Unified Security Platform - 28 Apr 2022
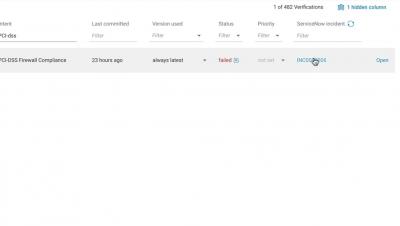
You’re tired of struggling with disjointed security information, incomplete integrations, and too much time and energy spent with multiple security vendors. These aren’t minor headaches of a managed services business, they ultimately drain efficiency and profits, and many are considering vendor consolidation as the answer.