AI Copilots and Developer Relations
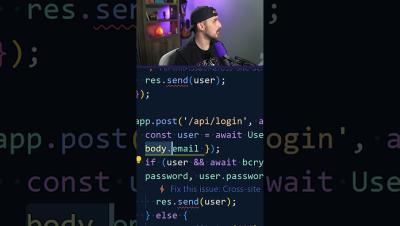
Welcome to Cloud Unfiltered! In this episode, host Michael Chenetz is joined by Erika Dietrick, a Developer Advocate at Cisco DevNet, fresh off her experience at Black Hat and DEF CON in Las Vegas. Erika dives into the evolving world of AI and its practical applications in development, with a focus on AI coding assistants like GitHub Copilot. Together, they explore.