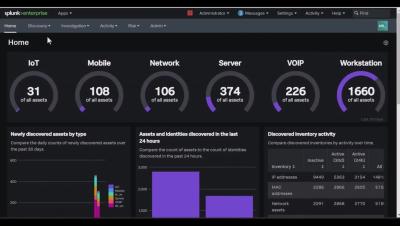
Splunk ARI Feature Video: Asset Discovery
Learn how the asset inventory provided by Splunk Asset and Risk Intelligence delivers a much-needed source of truth, bringing together different sources, helping to discover previously unknown assets, and delivering context and enrichment for key cybersecurity activities.