RKVST for Dropbox - bring provenance to your Dropbox files
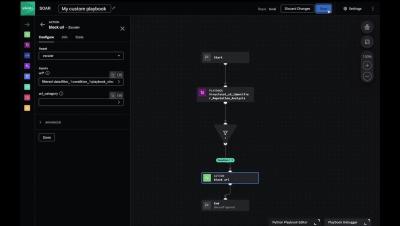
Bring provenance to your Dropbox files with RKVST. How can you prove that your work is original, authentic, and trustworthy? How can you protect it from being copied, manipulated, or misused? That’s where RKVST comes in, documenting the origin, history, and validity of your content, such as text, images, audio, or video, so you can prove where it came from. With RKVST you can: And with RKVST for Dropbox creating and recording the provenance metadata is as easy as a click of a button. Watch our video to find out how.