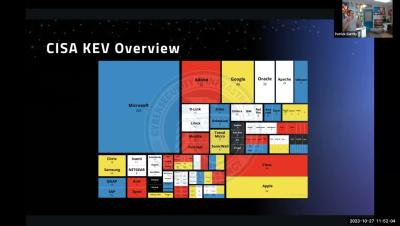
Grow Your Business with a 24/7 Security Operations Center (SOC) using Open Source Technologies.
Keeping IT Services profitable can be challenging, equipment and software costs increase, margins suffer and customers cancel. The solution resides in the economy of horizontal scale. Imagine what could happen if your existing customers contracted two times more services from your business, would that help? Sell them something every business needs: cybersecurity, launch your own Security Operations Center, and close new profitable deals. Why UTMStack and not something else? The answer is simple: UTMStack is free and Open source and very intuitive, so you can hit the ground up and running in no time.