Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Three Steps to Reduce False Positives and Alert Fatigue in Your SIEM
In the realm of cybersecurity, Security Information and Event Management (SIEM) systems are indispensable tools for monitoring and analyzing an organization’s security posture in real-time. However, one of the hurdles that security professionals often encounter is the prevalence of false positives which can overwhelm analysts and obscure genuine threats.
Harnessing the Magic of API: Turbocharging Business Automation
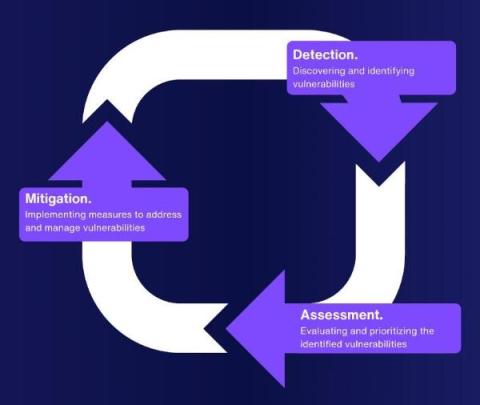
How to Streamline Vulnerability Management
The current cyber world is a veritable minefield, with problems and dangers evolving at a rate that far outstrips the ability of most organizations to respond. More than merely a technical issue, an organization's security posture is determined by the quality of its vulnerability management.
Understanding the Implications of Data Sovereignty and Why Data Residency may be a Better Choice for Your Business
The variety of cloud services that store organizational data continues to proliferate in type and number leading to tension as more governments, policymakers, and organizations consider (or are in the process of) implementing mandates requiring that specific types of data remain within geographical borders. Many organizations need to navigate these data management compliance mandates while also satisfying the competing needs of expediency, cost-effectiveness and, of course, data security.
Tines: scale by design and by default
The story of how Tines scales starts in the product with, well, a story. Any user of Tines will be familiar with the basic concepts of actions and events. They know that when an action receives an event, it runs in order to, e.g., transform that event data or send it off to an API. They also know that when the action has finished running, it will usually emit an event containing its results – an event that will then be sent onwards, to other actions, causing them to run in turn.
Weekly Cybersecurity Recap October 27
This week, many institutions were targeted for attacks, impacting thousands differently. In the northeast of the US, New York’s gambling scene suffered an attack, downing casinos across the state. In the South, hackers attacked Florida’s Akumin clinics, exposing patient data. In Pennsylvania, the City of Philadelphia suffered from leaking the information of city email owners.
University of Michigan Suffers Massive Data Breach Following Network Hack
The University of Michigan (UM) hosts more than 55,000 students, 35,000 staff members, and 640,000 alums. Unfortunately, following a recent cybersecurity breach, students, applicants, alums, employees, contractors, and donors may now have information at risk. The extent of the exposure is unknown, but the outcome could impact anyone. Those in association with UM must take steps to guard themselves before the assailants can misuse their information.
New Amazon-Themed Phishing Campaign Targets Microsoft Live Outlook Users
Several months ago, Netskope Threat Labs uncovered a surge in PDF phishing attachments infiltrating Microsoft Live Outlook. These attacks were part of a larger series of phishing campaigns aimed to trick unsuspecting users. Upon closer examination, it's now apparent that the majority of these campaigns centered around Amazon-themed scams, with occasional diversions into Apple and IRS-themed phishing attempts.
Job-to-be-Done: Quickly resolve exposures and vulnerabilities
It’s not unlikely that your team has a sufficient amount of vulnerability data that they must assess, prioritize, and remediate. Whether that’s a newly discovered vulnerability, an expired SSL certificate, or even a security policy breach – security teams need to get all this data into one place. For AppSec and ProdSec teams to be successful, they need to know which of their assets are exposed and vulnerable so they can take action to enable faster remediation.