Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Creating a Culture of Cybersecurity Part I: The 8 Benefits of Insourcing Your IT Help Desk
What is the culture of cybersecurity, anyway? When most people hear the phrase “Cybersecurity is a Culture,” their minds jump immediately to cybersecurity awareness training videos that help employees avoid phishing scams. Certainly, that is an important part of driving security awareness in your organization, but the true culture of cybersecurity is so much more. To quote our CTO, Jerald Dawkins, Ph.D., “Cybersecurity is a team sport.
Human-Crafted Phishing Emails Only Three Percent More Successful Than AI-Generated Ones, According To IBM
Red teamers at IBM X-Force warn that AI-generated phishing emails are nearly as convincing as human-crafted ones, and can be created in a fraction of the time. The researchers tricked ChatGPT into quickly crafting a phishing lure, then tested the lure against real employees.
Don't Take the Bait: Recognize and Report Phishing Attempts
Phishing attacks, which involve fraudulent attempts to trick individuals into divulging sensitive personal information, remain a significant threat. Despite advances in cybersecurity, hackers continue to adapt and evolve their tactics to exploit vulnerabilities.
CVE-2023-34048: Critical RCE Vulnerability in VMware vCenter Server and Cloud Foundation
What's New in Sysdig - October 2023
“What’s New in Sysdig” is back with the October 2023 edition! My name is Zain Ghani, based in Austin, Texas, joined by my colleague, Matt Baran, based in Los Angeles, California, to share our latest updates with you. The last few weeks have been really exciting at Sysdig.
Skeleton Keys and Local Admin Passwords: A Cautionary Tale
Picture yourself immersed in your favorite mystery novel, eagerly flipping through the pages as the suspense thickens. You’re enthralled, engrossed in the story of a hotel burglar with an uncanny ability to sneak into guest rooms without leaving telltale signs of break-ins or lock-picking. As you read on, you’re captivated – and stumped – by how this elusive bad actor can deftly close the doors behind them, leaving no clues.
PCI DSS Compliance Hardening Policy
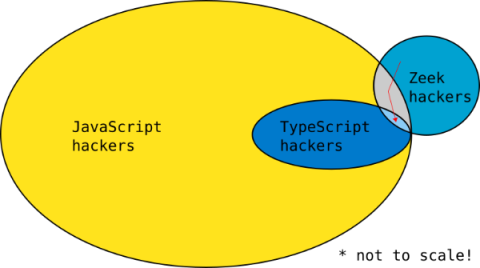
Writing a Zeek package in TypeScript with ZeekJS
Zeek® is the world’s most widely used network security monitoring platform and is the foundation for Corelight network evidence. In this blog I share how to write a Zeek package in TypeScript with a new capability called ZeekJS that was released as part of Zeek 6.0.
Revival Animal Health Network Announces Third-Party Data Breach
Headquartered in Orange City, Iowa, Revival Animal Health delivers business solutions for pet-oriented care and service providers; they offer pet healthcare products and animal supplies to pet professionals and individual pet owners. One way they provide services is via the e-commerce host CommerceV3. Revival Animal Health recently announced that CommerceV3 suffered a vulnerability, exposing 66,574 customer records.