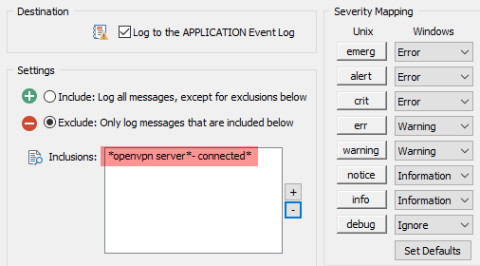
How Elastic AI Assistant for Security and Amazon Bedrock can empower security analysts for enhanced performance
Generative AI and large language models (LLMs) are revolutionizing natural language processing (NLP), offering enhanced conversational AI experiences for customer service and boosting productivity. To meet enterprise needs, it’s important to ensure the responses that are generated are accurate as well as respect the permissions model associated with the underlying content.