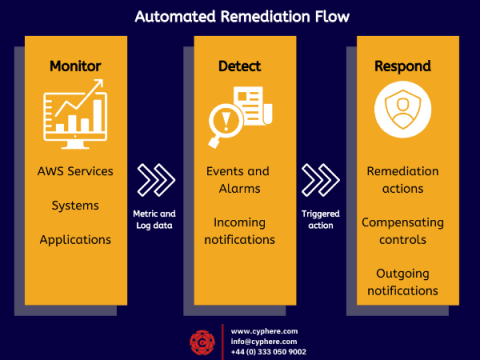
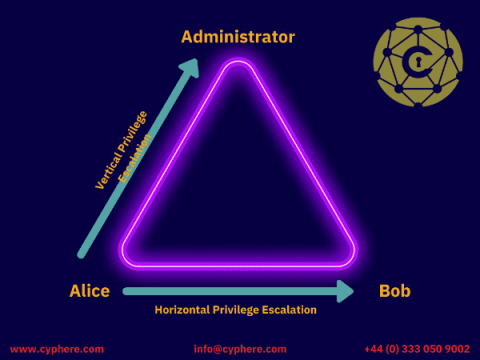
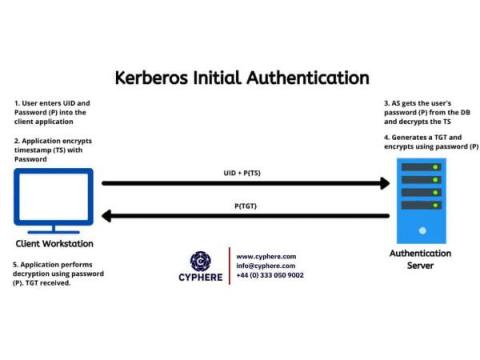
What is Database Security? Learn how to secure databases
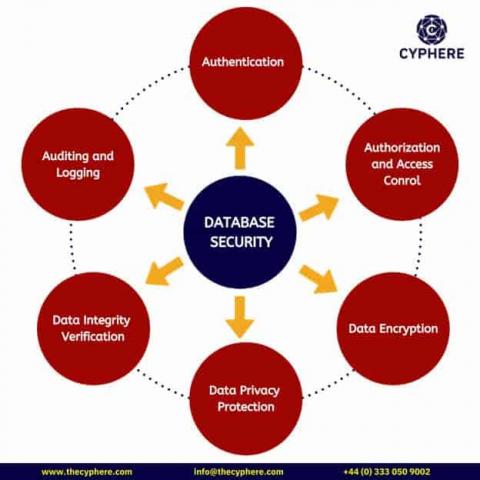
Databases are essential for organisations because they store data critical for the organisation to function. This data can include customer information, financial records, and contact details. Organisations need to access this data quickly and securely to make decisions and run their business. A database can help them do this by providing a centralised location for all their data.