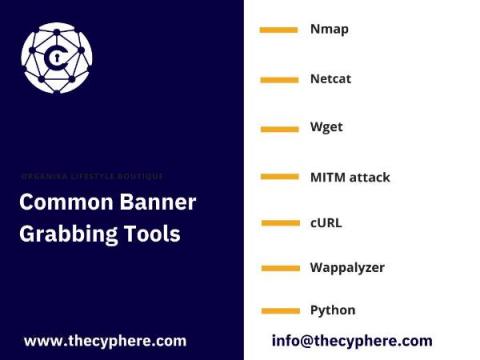
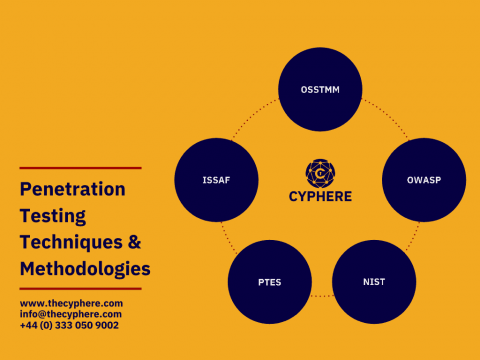
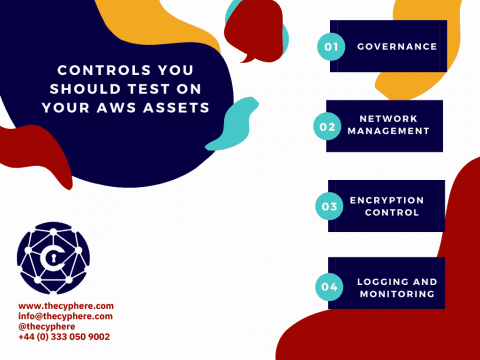
Wireless LAN Controller
Imagining a time without internet access at every point of life seems unimaginable now. The internet has been the greatest boon of the 21st century, and with wireless networking, man has progressed in leaps and bounds. It has ensured high efficiency, greater time management, increased productivity and lesser mess (no copper wires lying around). From homes to offices, students to working professionals, Wi-Fi is everyone’s go-to choice.