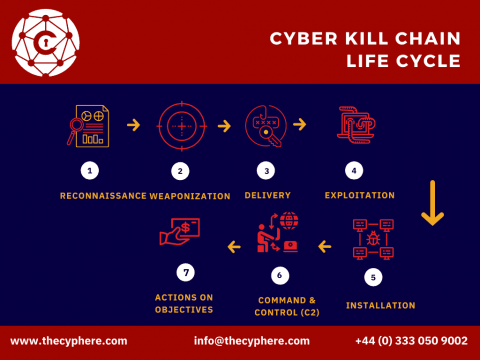
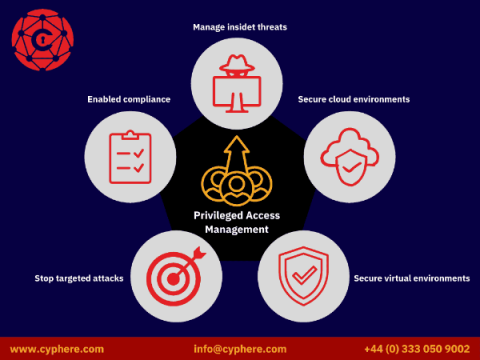
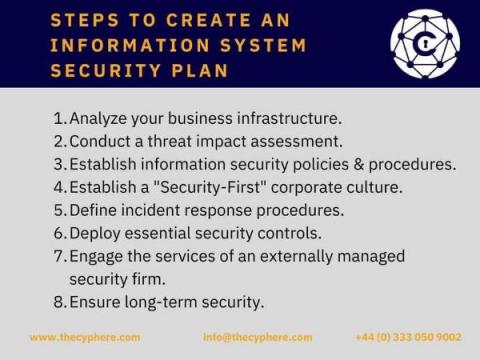
What is Lateral Movement in cyber security? Different ways to prevent it
Lateral movement refers to the techniques that a cyber attacker uses. Once getting access to a corporate network, the attackers don’t stop there. They move around throughout the entire network, owning more computers and user accounts while exfiltrating data at the same time. They escalate their privileges to gain access to higher permissions and eventually access more confidential, critical and sensitive data.