BYOD Security risks and best practices you can implement
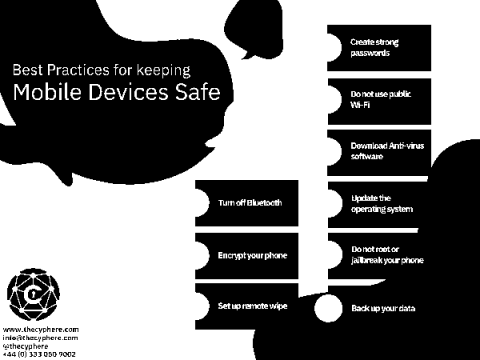
The trend of “bring your own device(BYOD)” is increasing in popularity as more and more employees use their devices for work purposes. While BYOD can offer many benefits to businesses, such as increased productivity and flexibility, it poses some security risks. To protect your business from these risks, it is essential to have your device policy in place.