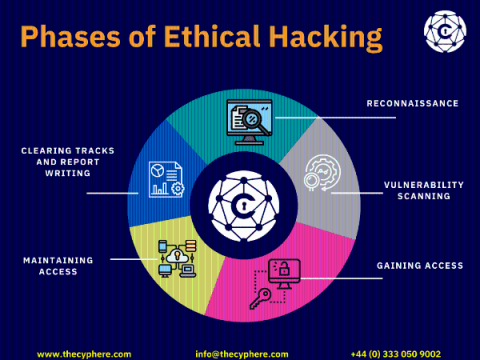
What is Ethical Hacking? Working, Techniques and Jobs
In the past, if someone called themselves hacker chances are, they received some backlash or negative connotations. However, in recent times as the field of information is on the rise a new term ‘Ethical Hacking’ has emerged and opened many different avenues for IT and cyber security professionals.