Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
DevOps
All About WhiteSource's 2021 Open Source Security Vulnerabilities Report
It’s that time of year again: WhiteSource’s annual State of Open Source Security Vulnerabilities for 2021 is here. Once again, when 2020 came to a close, our research team took a deep dive into the WhiteSource database to learn what’s new and what stayed the same in the ever-evolving world of open source security.
New Styra DAS Compliance Packs Foster Collaboration Across Teams
Bridging the gap between Security, Compliance and DevOps teams can be a challenging cultural shift to address. DevOps teams are eager to get software out faster and more efficiently, yet security best practices, like policy-as-code, need to be integrated from the outset to streamline the development process in this new cloud-native world.
Snyk @ Snyk: Enabling Kubernetes RBAC for Snyk's Developers
As Uncle Ben once said, “With great power comes great responsibility.” This is also true of the Kubernetes API. It is very powerful, and you can build amazing things on top of it, but it comes with a price—a malicious user can also use the API to do bad things. Enter Kubernetes RBAC (role based access control), which enables you to use the API in a controlled manner by granting only required privileges needed, following least privilege principle.
Automatically Assess and Remediate the SolarWinds Hack
With software supply chain attacks on the rise, are you wondering how you can recover quickly from the recent SolarWinds breach at your company? Months after its discovery, the devastating SolarWinds hack remains a top concern for business, government and IT leaders. This destructive supply chain attack put the spotlight on software development security — a critical issue for the DevOps community.
How SAML 2.0 Authentication Works?
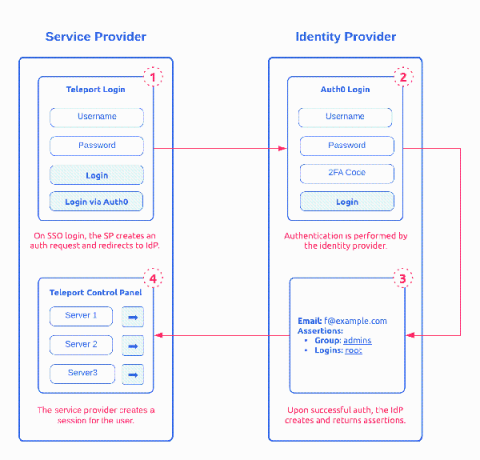
Security Assertion Markup Language (SAML) 2.0 is one of the most widely used open standard for authentication and authorizing between multiple parties. It’s one of the protocol that give users the single sign-on (SSO) experience for applications. The other adopted open standard is OAuth and OpenID. Of the two, SAML 2.0, released in 2005, remains the 800 pound gorilla in Enterprise SSO space. This post provides a detailed introduction on how SAML works.
Domain Controller: LDAP Server Signing Requirements
Datadog acquires Sqreen to strengthen application security
We began our security journey last year with the release of Datadog Security Monitoring, which provides runtime security visibility and detection capabilities for your environment. Today, we are thrilled to announce that Sqreen, an application security platform, is joining the Datadog team. Together, these products further integrate the work of security, development, and ops teams—and provide a robust, full-stack security monitoring solution for the cloud age.
Python language support now beta in Snyk Code
Snyk Code now offers beta support for Python 2.x and 3.x projects. You do not have to install or update anything since we added the support to the backend engine and it is available instantly to be used. When a repository is scanned, you will see Python beta results showing up. If you cannot wait for a scheduled rescan, you can manually trigger a scan.
CloudCasa Now Supports Data Protection for Amazon RDS
The choice for persistent storage for your cloud native applications depends on many factors including how your cloud journey started and whether your applications were migrated or developed for the cloud. Also, depending on how early you started using containers and migrated to Kubernetes, your distribution or managed service may not have offered the persistent data services you needed.