A Comprehensive Guide to Azure Data Security
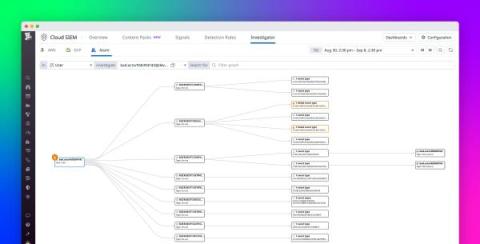
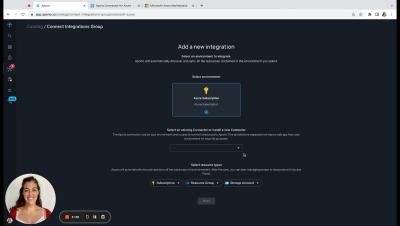
In our interconnected world, the value of data is growing with cyber threats also on the rise. This causes the security and protection of data to become crucial. Organizations have become compelled to adopt strict measures to safeguard their data. Implementing security practices in data protection and encryption ensures the confidentiality, integrity, and availability of the data stored in the cloud.