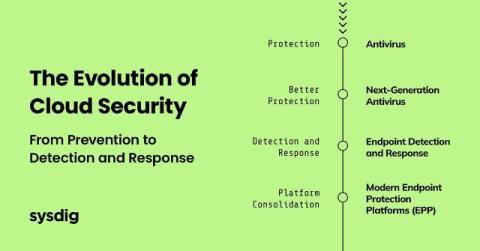
Azure DevOps - Now With Added Veracode
Veracode is pleased to announce the general availability of our new Azure DevOps Workflow integration. This new integration provides our customers using Azure DevOps Services with easy-to-configure, event-driven security testing of their application and infrastructure code managed in their Azure DevOps Repos.