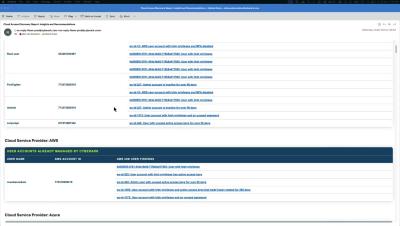
Falcon Cloud Security Asset Graph: Demo Drill Down
Gain the edge in the race against adversaries by leveraging unified visibility across your attack surface—from endpoint to cloud. See how Falcon Cloud Security's Asset Graph uncovers vulnerabilities, highlights misconfigurations, and automatically maps the complete attack trajectory, empowering you to respond faster and mitigate threats effectively.