Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Cloud
Demo - Introduction to Netskope SaaS Security Posture Management (SSPM)
Reckless to Fearless: Automating Remediation in the Cloud
Straight Talk Series: Network and Security United
Ask SME Anything: What's the difference between SASE and SSE?
Who Do You Trust? Challenges with OAuth Application Identity
In our recent blog, Who Do You Trust? OAuth Client Application Trends, we took a look at which OAuth applications were being trusted in a large dataset of anonymized Netskope customers, as well as raised some ideas of how to evaluate the risk involved based on the scopes requested and the number of users involved. One of the looming questions that underlies assessing your application risk is: How does one identify applications? How do you know which application is which? Who is the owner/developer?
Collaborate Seamlessly with Egnyte and Google Workspace
Today’s organizations utilize a multitude of solutions to create, share and manage their sensitive content. That business reality is exacerbated by additional cloud file storage solutions that result from acquisitions, competing employee preferences, or shadow IT initiatives. So, it’s no surprise IT teams struggle to manage and control document and file system sprawl.
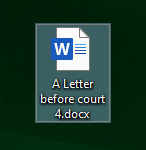
Microsoft Office Document Triggering New Zero-Day
Most ransomware groups operating in the RaaS (Ransomware-as-a-Service) model have an internal code of A new zero-day vulnerability (CVE-2021-40444) affecting multiple versions of Windows has recently been discovered and disclosed by Microsoft. According to Microsoft’s Security Update Guide, the MSHTML component can be exploited by an attacker through a custom ActiveX control, allowing remote code execution.
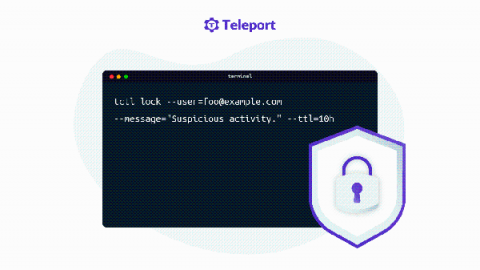
Security Incident Containment with Teleport Session and Identity Locking
What would you do when a security incident is detected? Shut down the servers? Pull out the power cord from the data center? When an incident is detected, both the incident method and the time required to contain an incident are essential to limit the damage. The slower you are to react, the more damage an incident would incur. And a service downtime to contain an incident can cost businesses even more than a security incident itself.