Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Application Security
The latest News and Information on Application Security including monitoring, testing, and open source.
Top 6 DevOps Web Application Security Best Practices
In today’s world, the importance of incorporating web application security best practices cannot be overstated. Recent studies show that web applications are the top attack vector in nearly 80% of incidents. The good news is DevOps processes lend themselves to integrated security practices. Here are the top six best practices for seamlessly weaving web application security into DevOps.
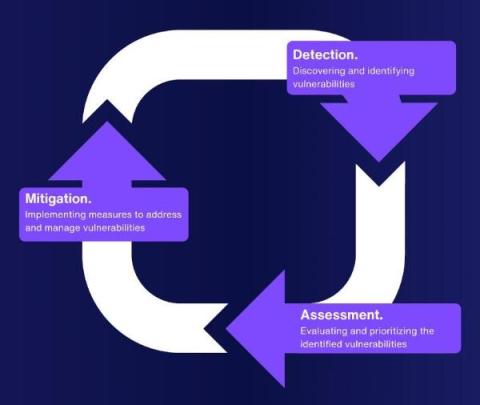
How to Streamline Vulnerability Management
The current cyber world is a veritable minefield, with problems and dangers evolving at a rate that far outstrips the ability of most organizations to respond. More than merely a technical issue, an organization's security posture is determined by the quality of its vulnerability management.
This Month in Datadog: Heatmaps Updates, API Catalog, Content Packs for Cloud SIEM, and more
Add to Your AppSec Arsenal with Mend.io's Integration with Secure Code Warrior
We’re delighted to announce that Mend.io has launched a new integration with Secure Code Warrior®, a platform that provides secure coding training and tools that help shift developer focus from vulnerability reaction to prevention.