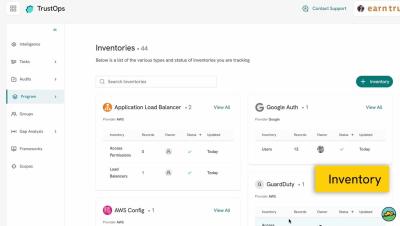
Inventory - What is it? How can you use it as evidence?
An inventory is a specific list of data that is gathered to provide information about a certain part of the business. The inventory is inspected by an automated test or by a human to determine if one or more controls are satisfied and to analyze the results of the inventory. Examples of inventories are users, security incidents, devices, servers, databases, logs, etc.