Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Code similarity analysis with r2diaphora
Binary diffing, a technique for comparing binaries, can be a powerful tool to facilitate malware analysis and perform malware family attribution. This blog post describes how AT&T Alien Labs is leveraging binary diffing and code analysis to reduce reverse-engineering time and generate threat intelligence.
Cloud Infrastructure Entitlements Management (CIEM) with Sysdig Secure
Discover what CIEM Security is and how easy it is to implement with Sysdig Secure for cloud. Over-permissioned accounts and roles is the most common cloud service misconfiguration security problem. Implementing least privilege is a crucial best practice to avoid or mitigate risks of data breaches and contain privilege escalation and lateral movement.
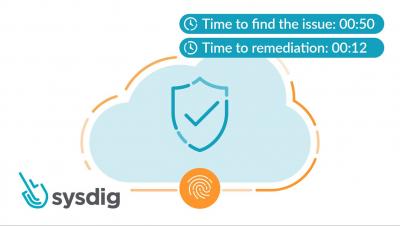
Remediating Excessive IAM permissions in less than 2 minutes with Sysdig Secure
Snyk Code adds Apex, Swift language support + API, GraphQL security
Snyk Code has had a tremendous 2021. It started the year supporting three languages — Java, JavaScript, and TypeScript — and has since added Python, C#, PHP, Ruby, and Go. More languages and features are on the horizon, and in this article, we’re happy to announce the addition of Swift and Salesforce’s Apex support, as well as API and GraphQL security. Let’s get into it!