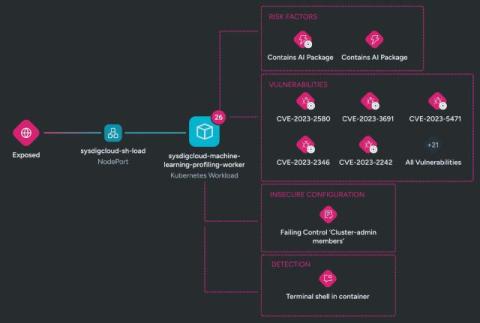
Sysdig's AI Workload Security: The risks of rapid AI adoption
The buzz around artificial intelligence (AI) is showing no sign of slowing down any time soon. The introduction of Large Language Models (LLMs) has brought about unprecedented advancements and utility across various industries. However, with this progress comes a set of well-known but often overlooked security risks for the organizations who are deploying these public, consumer-facing LLM applications.