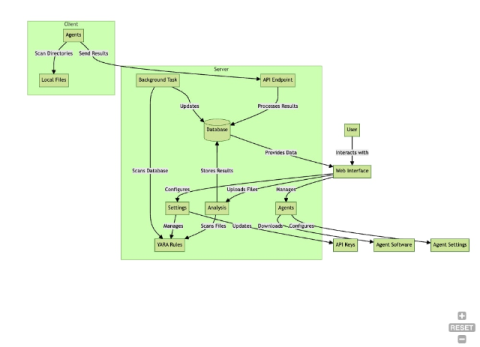
Why Am I Getting So Many Spam Calls?
You may be receiving an increase in spam calls if your phone number is on the dark web or people search sites, if you’ve answered spam calls in the past or if your phone number was leaked in a data breach. Spam calls are unwanted calls that could be from telemarketers, robocallers or scammers. Although some spam calls are simply unsolicited, scam calls fall under the category of spam calls but are different due to their malicious nature.