Understanding the Dora Compliance: A Comprehensive Guide
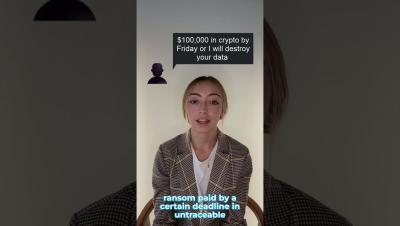
Technology is always brimming with advancements, and it is more prominent in the financial sector. As financial institutions increasingly rely on digital infrastructure to enhance operations, customer experience, and security, they also face growing challenges in mitigating the risks that come with it, such as cyber threats, system failures, and other operational vulnerabilities.