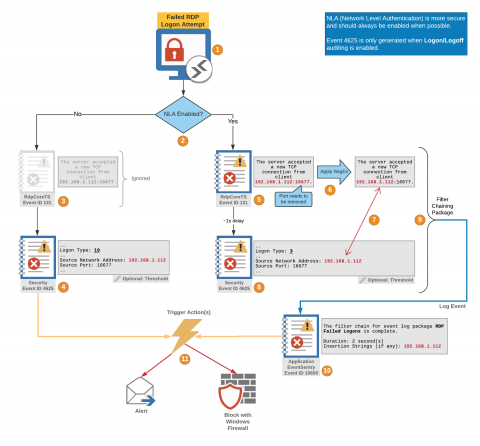
Prevent Wordpress hacking using this Pen Testing guide
Welcome back to the next edition of “Hacking WordPress”. Find Part 1 if you missed it. Let me start with a PSA message. It is illegal to hack, log in to, penetrate, take over or even hack, a system or network of systems without the explicit permission of the owner. Criminal hacking is illegal and punishable under Federal Law. I am describing methods to learn more about WordPress so you can protect your sites better.