Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Coronavirus: 10 Steps Employers Should Take to Maintain a Safe Workplace
As we’re actively in the throes of COVID-19, it’s understandable that workers and employees are uneasy about their safety and security on the job. Here are 10 steps employers need to take to keep your workplace safe in the face of a public health emergency.
DevSecOps Best Practices with JFrog Platform
Application Security Testing Trends
According to a recent Forrester report, the application security market will exceed $7 billion by 2023, with security scanning tools leading. Clearly, organizations increasingly understand that securing their application layer is important, and they are prepared to invest substantial resources in protecting it.
CyberGRX vs UpGuard Comparison
Robust vendor risk management practices has never been more important. It is increasingly one of the top concerns of CISOs around the world. This is because outsourcing, digitization, and globalization have changed the way we do business over the last few decades. These forces have led to innovation in products and services, the ability to focus on core competencies, reduced costs, and new global markets.
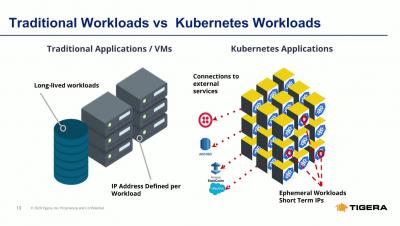
The Future is Hybrid: Practicing Security in the Hybrid Cloud
By now, many organizations have adopted the cloud in some way. We saw organizations moving whole servers over to the cloud at the beginning, but now we see small parts of a system being moved to the cloud and new cloud native offerings. We’ll use the analogies of Lincoln Logs and Legos to describe these deployment models.
Third-party data breach exposes GE employees' personal information
Past and present employees of General Electric (GE) are learning that their sensitive information has been exposed by a data breach at a third-party service provider. Fortune 500 company GE says it was recently informed of a security breach at one of its partners, Canon Business Process Services.
Working Anywhere With Egnyte: Mobile Guide
In recent weeks, companies and organizations that ordinarily operate in a more “traditional” office environment have had to pivot quickly to flexible and alternative working arrangements. At Egnyte, our goal has always been to help provide safe, secure access to your content no matter where you are, and that goal has become increasingly more important in the current climate.
Elastic SIEM is free and open for security analysts everywhere
Security teams must protect attack surfaces that are becoming bigger and more distributed due to the growth of remote work, cloud infrastructure, and other dynamics. These teams understand that meeting this challenge at scale requires the successful incorporation of the appropriate technology into their security operations program.
Use the Node.js HTTP Module to Make a Request
The ecosystem around making requests in Node.js applications is huge. With countless libraries available, it can be helpful to understand why they exist. This helps to improve your understanding of Node.js as a whole, and makes choosing an HTTP client easier. In the first post in this series, we looked at creating servers using Node's http module. In this post, we will explore making a request using the http.request method and handling the response.