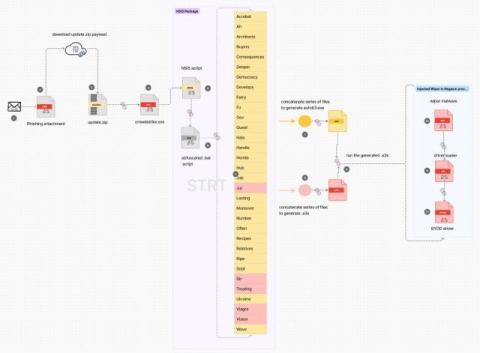
CISA's Secure By Design: A Year Later
In April this year, the CISA Secure By Design initiative turned one. The initiative calls for the public and private sectors to work together to challenge and encourage software manufacturing companies to adopt principles to ensure their software is developed and produced as securely as possible. The initiative tracks seven goals that software manufacturers can pledge to develop and transparently track progress towards those goals.