Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
What Could Losing One Terabyte of Data Cost Your Business?
It’s no secret that your digital footprint is growing. Whether your business has 10 employees in one office or 2,000 employees in offices all over the world, you’re creating more content today than you did two years ago—or 2 months ago for that matter. Along with increased volume, content itself has evolved to encompass much richer media, like HD videos and CAD files.
Understanding the Types of Risk in the Oil & Gas Industry
Defined as critical infrastructure, the oil & gas industry increasingly faces cybersecurity risks as nation-state cybercriminals attempt to undermine other countries. The integration of information technology (IT) systems into operational technologies (OT) creates a unique threat to the oil and gas industry that places both the companies and the public at risk.
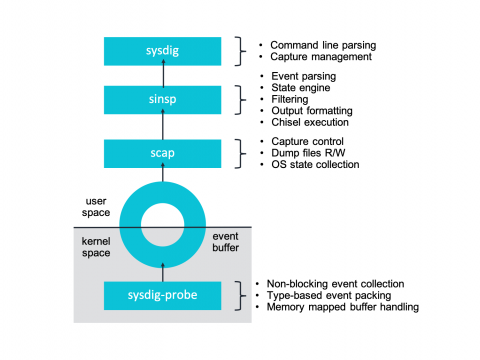
Sysdig and Falco now powered by eBPF.
At Sysdig we’ve recently undergone a pretty interesting shift in our core instrumentation technology, adapting our agent to take advantage of eBPF – a core part of the Linux kernel. Sysdig now supports eBPF as an alternative to our Sysdig kernel module-based architecture. Today we are excited to share more details about our integration and the inner workings of eBPF. To celebrate this exciting technology we’re publishing a series of articles entirely dedicated to eBPF.
What's Hiding On Your ICS Network?
Trends in Industrial Control Systems Cybersecurity
With connectivity to the outside world growing, cyber attacks on industrial computers constitute an extremely dangerous threat, as these types of incidents can cause material losses and production downtime for a whole system. Moreover, industrial enterprises knocked out of service can seriously undermine a region’s social welfare, ecology and macroeconomics. Not surprisingly, cybersecurity is therefore becoming more and more important across the board.
AT&T Cybersecurity Is Born
Today marks another new milestone and I am proud to unveil our new name….AlienVault has now combined with AT&T Cybersecurity Consulting and AT&T Managed Security Services to form a new standalone division, AT&T Cybersecurity!
Detectify now checks for Drupal RCE (CVE-2019-6340)
On February 20th, Drupal released a security update that fixes a critical remote code execution vulnerability. Detectify scans your site for this vulnerability and will alert you if you are running a vulnerable version of Drupal.
Do Security Cameras Undermine your Authentication?
For various reasons, many executives and senior team members with privileged status on the network and/or access to financial assets oftentimes need to access corporate IT systems from a public place outside the office. What is very common in these types of places is that they’re covered with security cameras.
Vulnerability Management and Patch Management Are Not the Same
Vulnerability management and patch management are not products. They are processes, and the products are tools used to enable the process. You cannot buy a hammer, nails and wood and expect them to just become a house, but you can go through the process of building the house or hire someone to do it for you as a service.