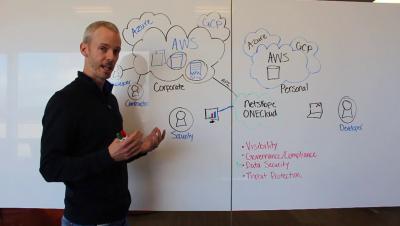
A Multi-Million Dollar Commitment to Our Multi-Cloud Strategy
Every business today is growing in their own unique way. Their infrastructure is made up of a combination of cloud and on-premises repositories. Their application suite is custom built with a myriad of productivity applications like Slack, Office 365, Zoom, and more. And finally, their users are working on a wide range of devices, from Apple iPhones to Microsoft Surface Pros. The common theme amongst businesses is their need for flexibility.