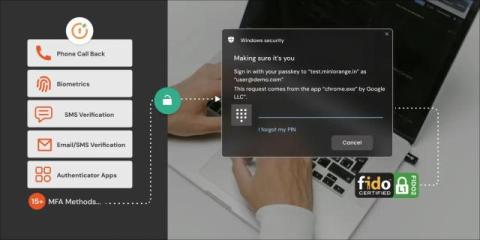
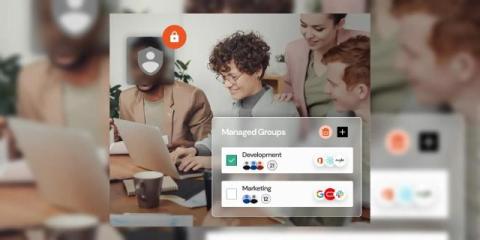
miniOrange Customer Success Story of Mondo Informatica for ASP.NET Applications
Simone Tusino, Director of Mondo Informatica, an Italian IT Solutions provider company, shares his experience with the miniOrange ASP.NET Applications, highlighting miniOrange’s exceptional products, services, and support in this video testimony. Implemented Single-Sign-On between.NET based Platform developed by Mondo-Informatica for their key client with Shibboleth 3 efficiently saving the valuable time of the end users and completing the project with a fixed budget.