A Comprehensive Guide to PCI Compliance Test
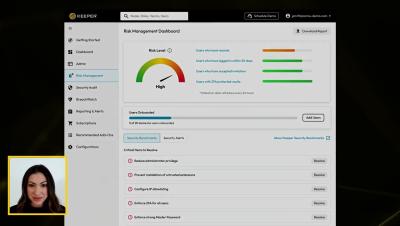
Because online shopping is so important to us now, keeping payment information safe is very important. Payment Card Industry Data Security Standard (PCI DSS) was created to protect cardholder information that is private and to stop fraud. PCI DSS must be followed by any organization that handles, saves, or sends cardholder data. A Very Important Step: The PCI Compliance Test Organizations must go through a lot of tests and evaluations to show that they follow PCI DSS.