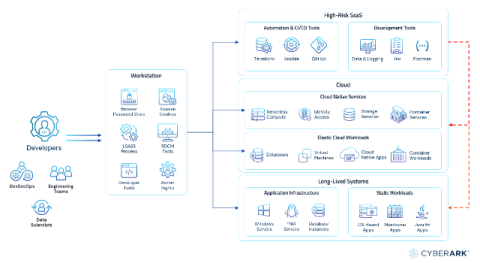
Stop Letting Security Audits Go to Waste-They're More Than Just a Checkbox Exercise
Over the past two decades, data has become a critical asset for nearly every organisation. Consequently, a variety of regulations and industry standards now govern business operations. In today’s data-driven age, certification through security audits serves as a testament to an organisation’s adherence to industry standards, regulations, and security measures.