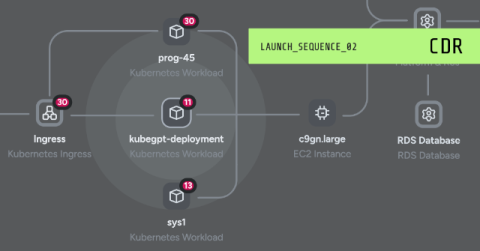
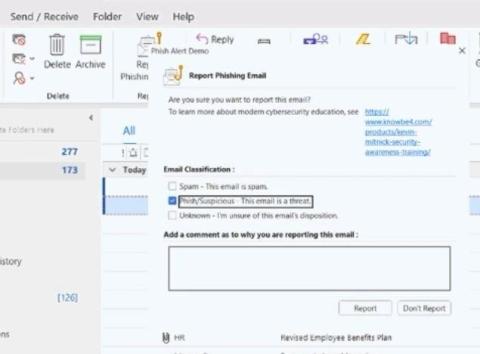
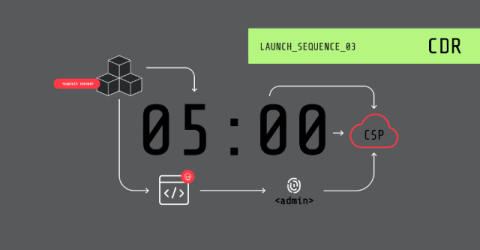
Black Box Security Testing - Process, Types and Techniques
With cybercrime costs projected to hit $10.5 trillion by 2025, securing digital assets is more critical than ever. Black box testing in security has become a key strategy for organizations to identify vulnerabilities in software and systems proactively. This blog delves into the essential role of black box security testing in mitigating risks along with its various types and techniques.