Using Coralogix to Gain Insights From Your FortiGate Logs
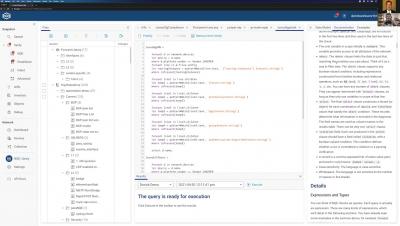
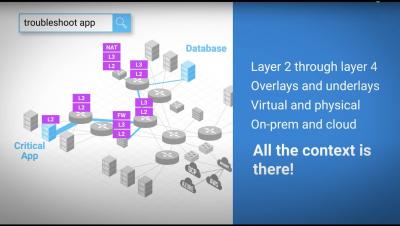
FortiGate, a next-generation firewall from IT Cyber Security leaders Fortinet, provides the ultimate threat protection for businesses of all sizes. FortiGate helps you understand what is happening on your network, and informs you about certain network activities, such as the detection of a virus, a visit to an invalid website, an intrusion, a failed login attempt, and myriad others. This post will show you how Coralogix can provide analytics and insights for your FortiGate logs.