Keeper vs Dashlane: Comparing Password Management Solutions
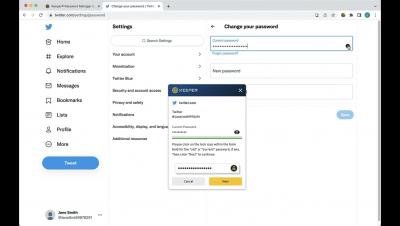
Keeper Security and Dashlane are both password management solutions that offer various user features and benefits. While Dashlane is a basic password manager with a password generator tool, Keeper is a robust, enterprise-grade solution that is only one part of a suite of cybersecurity tools covering password, secrets and connection management. Dashlane allows businesses to instantly generate and save strong passwords for all employee logins. It is supported on desktops, laptops and mobile devices.