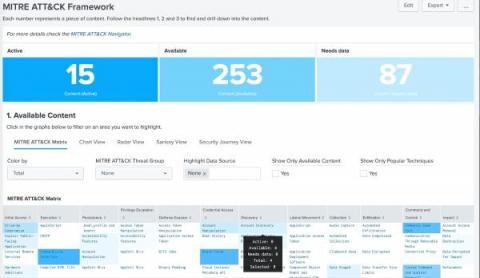
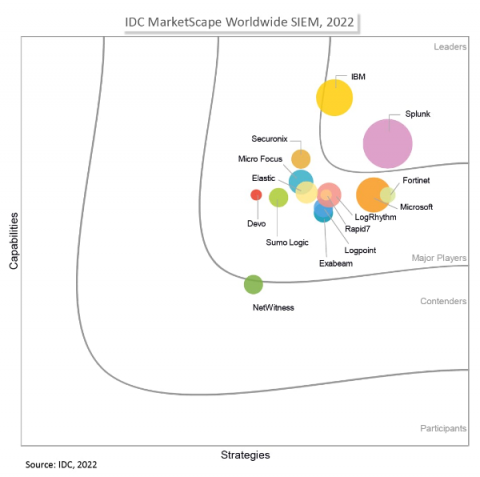
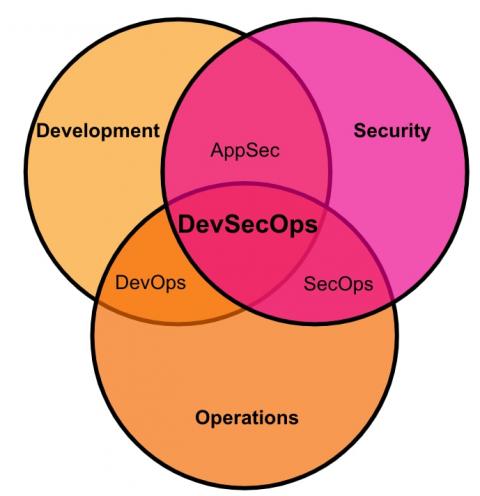
Using Splunk to Secure Your Productivity and Team Collaboration Environment
Productivity and collaboration tools are key components for any business today – we use mail, docs, spreadsheets, shared whiteboards and many other cool tools daily. In this post, we will talk about how Splunk helps teams work and collaborate securely while using Google Chrome and Google Workspace.