Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
Lockdown Ransomware Before it Spreads
AS Roma Football Club Scores Big with Egnyte
Modernizing Infrastructure and Creating Secure Collaboration for Their Global Organization
Business Email Attack Losses Now Top $12 Billion - FBI
The U.S. Government’s Federal Bureau of Investigation (FBI) released an open administration declaration this week cautioning that ‘business email compromise’ (BEC) scamming emails are on a dramatic increase Globally.
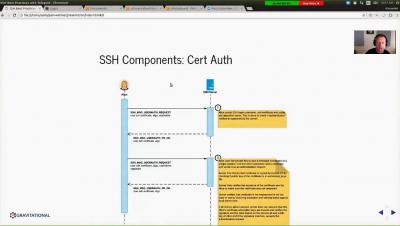
Privileged Access Management Best Practices Using SSH and Teleport
Autonomous cars: Data will drive the future
You might have not noticed it, but we are on the verge of a disruptive change in the way we humans transport ourselves. In the next five to ten years the way we think about – and take – our daily commute, our holiday vacation, trips to the market – anything that involves transport over a distance too great to walk – will dramatically change.
Questions You Should Ask Your Cloud-Based Log Management Service Provider
The log management service is often outsourced to a third-party service provider due to the complexity of the process involved in the collection of logs. When a business plans for outsourcing log management to a service provider, business requirements must be given a top-most priority. To start with, a business must identify the goals it desires to accomplish through log management. After locating the required resources, the decision-making body should select a vendor for availing its services.
Got Container Security? Make Sure to Secure Code and Supplemental Components
Organizations face numerous primary threats and security concerns when it comes to their container environments. Those issues extend into their build environment, an area which organizations need to protect because it’s usually the least secure aspect of their container infrastructure. They also extend into other areas, including inside the containers themselves.