Overcoming the 3 biggest challenges in system hardening
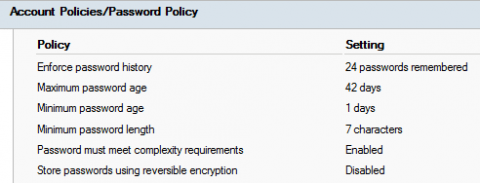
As delivered from the manufacturer, your network systems’ default configurations are often function-oriented rather than security-oriented. Changing the system’s default configuration to a more secure form is what we refer to as system hardening.