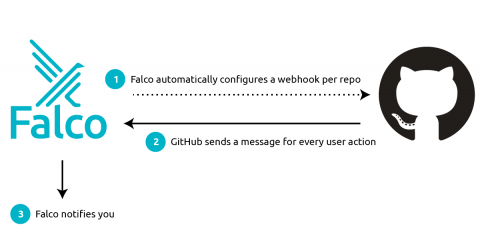
Responding to the Dropbox Breach with a Falco GitHub Plugin
On November 1st, Dropbox disclosed a security breach where the attackers stole over 130 code repositories after gaining access to one of the employee’s GitHub accounts using the stolen credentials of that employee via a well-designed phishing attack.