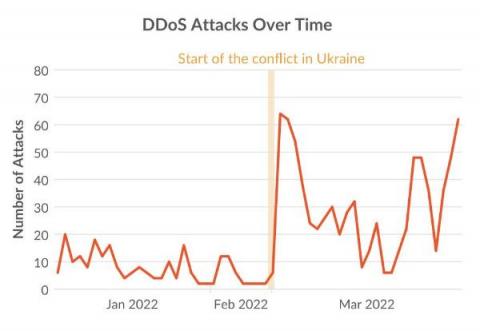
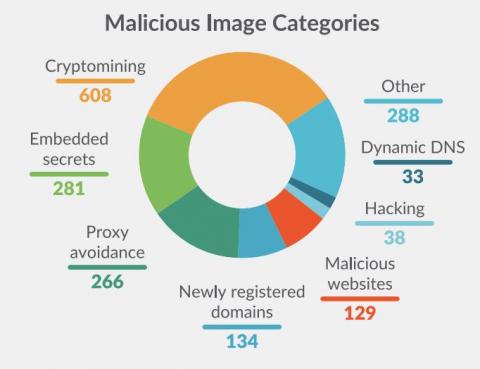
Top 15 Kubectl plugins for security engineers
Let's dig deeper into this list of Kubectl plugins that we strongly feel will be very useful for anyone, especially security engineers. Kubernetes, by design, is incredibly customizable. Kubernetes supports custom configurations for specific use case scenarios. This eliminates the need to apply patches to underlying features. Plugins are the means to extend Kubernetes features and deliver out-of-the-box offerings.