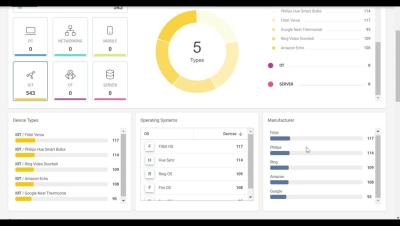
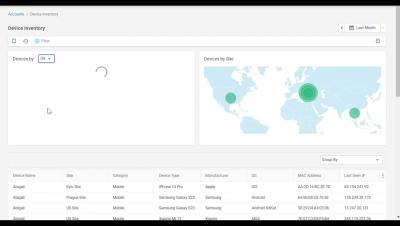
Arctic Wolf Labs Observes Threat Campaign Targeting Cleo MFT Products - Remediation Guidance
Update: Dec 11, 2024. Find the latest information in our follow-up security bulletin. On December 7, 2024, Arctic Wolf began observing a novel campaign exploiting Cleo Managed File Transfer (MFT) products across several customer environments. Initial indications of malicious activity in this campaign were identified as early as October 19, with a sharp increase in early December.