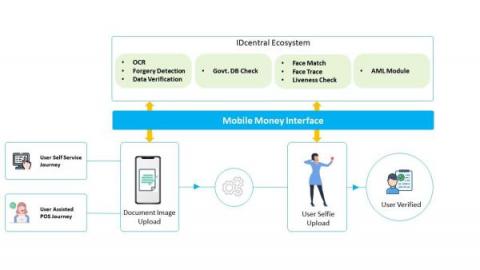
An Alleged 22 Billion Mobile Money Fraud
As per the news reports published MTN’s Mobile Money Bank suffers N22B Fraud, Drags 18 Banks to court for recovery The newly licensed Mobile Money Payment Service Bank Limited (MOMO PSB) a banking subsidiary of MTN Communications Limited has in less than a month operation suffered a massive fraud worth over N22 billion on its network. The suspicious transfers were due to the fact that the MoMo PSB suffered system exploitation which led to the said debits.