Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Access Management
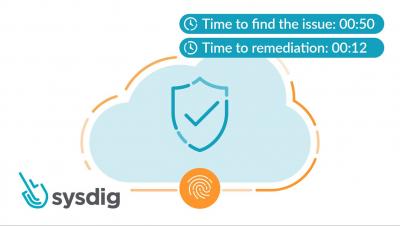
Remediating Excessive IAM permissions in less than 2 minutes with Sysdig Secure
Axis Security Wins 2021 CISO Choice Award for Best Startup Security Company
Free Webinar | What's new in PAM360
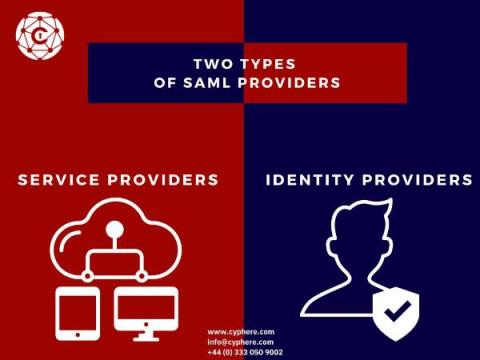
What is SAML Authentication? Is it different from OAuth
SAML authentication is a must for organisations that want to do federated identity and single sign-on. These applications require both sides of the service or application to use a common set of credentials for identification and authorization. This is an effort to reduce security risks, increase the availability of services through more robust authentication, improve reliability by leveraging existing investments in infrastructure, and improve the end-user experience.
Why access management needs to evolve beyond passwords
Access management is a key element of any enterprise security program. Using policies defined by IT administrators, access management enforces access rights across the network. It does this by designating which groups of users are allowed access to which applications and identifying which user attributes are required to access each application. Problems arise for businesses when they base their access management programs entirely around passwords, however.
Privileged Access Management (PAM) with Netwrix Solution
Top 5 Things People Hate About PAM
Privileged access management (PAM) solutions have been around in various forms for decades now. Whether you want a password vault, session management, reduced privilege or a combination of privileged management workflows, there’s been no shortage of vendors to choose from. So why does the thought of PAM still make admins shudder? Surely, it should be enjoyable to have a PAM solution humming along, reducing your organization’s risk while you, the admin, focus on your other duties.
What is Privileged Access Management (PAM)? Definition & Examples
As organizations migrate to the cloud and adopt more “as-a-Service” technologies, identity and access have become the perimeter. Remote workforces mean that limiting access according to the principle of least privilege is a fundamental security control. As part of securing applications and networks, organizations need to focus on users with privileged access because they pose greater insider and credential theft risks.
User Entitlement Review Explained
The entitlement review definition is simple: a review of user access permissions and other rights. The goal of a user entitlement review is to ensure that each user in the IT environment has access to the data they need to do their job and nothing more — the principle of least privilege. A structured and regular entitlement review process helps mitigate security risks and protect sensitive data.