Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Git
Cybersecurity and AI deep in the heart of Texas Cyber Summit
Dive into our Texas Cyber Summit 2023 recap. Discover how AI is impacting cybersecurity, learn about Zero Trust strategies, ransomware dos and don'ts, and more.
Protecting Your Software Supply Chain: Understanding Typosquatting and Dependency Confusion Attacks
Typosquatting and dependency confusion are two common tactics used by hackers to exploit open-source package repositories. Understand how these attacks work and discover preventive measures to secure your infrastructure.
Hands-on guide to Runtime Security for CI/CD Pipelines with StepSecurity
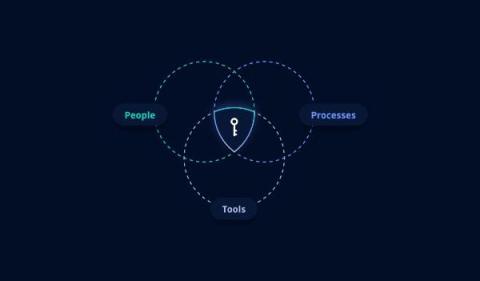
Secrets management takes more than just tools
Can you just purchase a tool to give you good security posture? Discover how People, Processes, and Tools elevate code security to protect against data breaches.
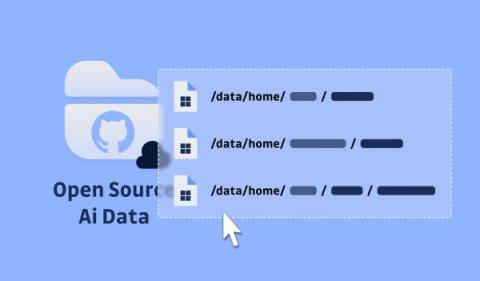
Microsoft AI involuntarily exposed a secret giving access to 38TB of confidential data for 3 years
Discover how an overprovisioned SAS token exposed a massive 38TB trove of private data on GitHub for nearly three years. Learn about the misconfiguration, security risks, and mitigation strategies to protect your sensitive assets.
A look at the future of supply chain and national security: Updates from CISA and NIST
Explore CISA & NIST's recent cybersecurity publications. Get key insights into securing vital infrastructure in an ever-evolving threat landscape and how GitGuardian can help.
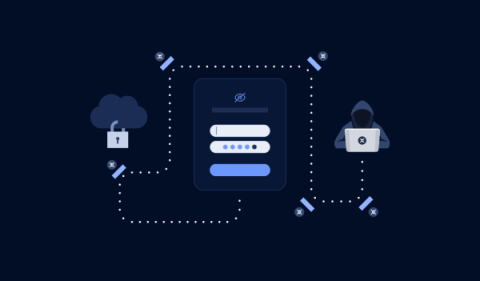
From GitHub Leak to Pwn: A Hacker's Kill Chain
Discover how seemingly minor mistakes, like leaking a secret to a non-publicly accessible resource, can lead to a major breach. In this engaging scenario, see how an attacker would chain vulnerabilities to access highly sensitive areas, and learn a valuable lesson along the way.
Honeytoken Adventure: From Beta to Beyond
Read the journey of GitGuardian Honeytoken, a tool that is changing the game in supply chain protection and threat detection. Explore its features, the motivation behind its creation, and what's next.
Three Recent Examples of Why You Need to Know How Vulnerable Your Secrets Are
In today's digital landscape, the issue of compromised credentials has become a major concern. Discover how renowned companies like Microsoft, VMware, and Sourcegraph were recently confronted with the threats of secrets sprawling.