It's Time to Get Hip to the SBOM
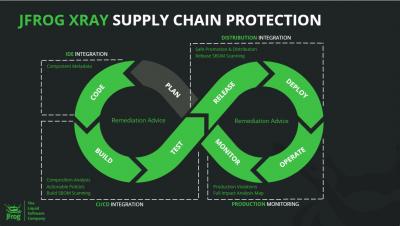
The DevOps, IT security and IT governance communities will remember 2021 as the year when the Software Bill of Materials , or SBOM, graduated from a “nice to have” to a “must have.” Around for years, the SBOM has now become a critical DevSecOps piece, which everyone must thoroughly understand and incorporate into their SDLC (Software Development Lifecycle).