Log4j Detection with JFrog OSS Scanning Tools
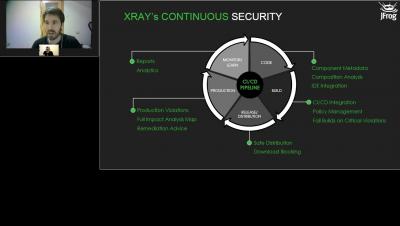
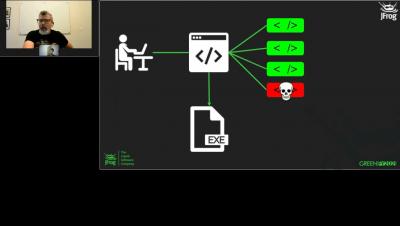
The discovery of the Log4Shell vulnerability in the ubiquitous Apache Log4j package is a singular event in terms of both its impact and severity. Over 1 million attack attempts exploiting the Log4Shell vulnerability were detected within days after it was exposed, and it may take years before we see its full impact.