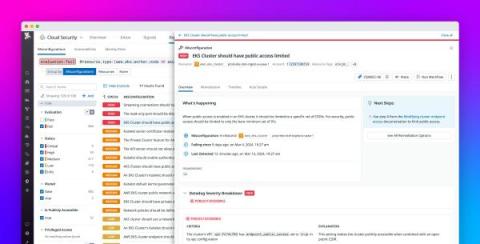
Monitor your Kubernetes security posture with Datadog Cloud Security Management
In recent years, the popularity of Kubernetes deployments has surged—as has the prevalence of security risks associated with the technology. Red Hat’s State of Kubernetes Security for 2023 reveals that 67 percent of organizations have encountered delays in application deployments due to Kubernetes-related security issues. Additionally, 37 percent have experienced significant revenue or customer losses stemming from Kubernetes security incidents.